【専用出品】ホットランド 株主優待券 分
(税込) 送料込み
商品の説明
2024/3月末まで
商品の情報
| カテゴリー | チケット > 優待券/割引券 > レストラン/食事券 |
|---|---|
| 商品の状態 | 新品、未使用 |

株式会社ホットランド(銀だこ)株主優待券1,000円分

たなたなりんだっしゆ様専用)ホットランド株主優待1万5千円分(期限9

新商品!新型 銀だこ 株式会社ホットランド 株主優待券1,000円分 | cenou.bf

ホットランド株主優待券15000円分 銀だこ 小物などお買い得な福袋

専用】ホットランド(銀だこ) 株主優待券 6000円分 | svetinikole.gov.mk

廉ちゃん様専用】ホットランド株主優待 銀だこ【15,000円分】 www

マクドナルド株主優待券 3冊とホットランド(銀だこ)500円券 1枚

tadasi様専用 ホットランド株主優待券 12000円分 築地銀だこ

2023年最新】株主優待 ホットランドの人気アイテム - メルカリ

在庫処分】 tadasi様 ホットランド 株主優待券 円分 銀だこ - www

小物などお買い得な福袋 築地銀だこ ホットランド株主優待 500円分 500

たなたなりんだっしゆ様専用)ホットランド株主優待1万5千円分(期限9

ホットランド 株主優待券 1500円分の通販 by りさこ's shop|ラクマ

www.haoming.jp - 株式会社ホットランド 優待券1枚 500円分

開店記念セール!】 桜餅太郎様専用 銀だこ 株主優待券 36枚 分

ホットランド 銀だこ 株主優待券 20000円分 注目 stockshoes.co

セール 登場から人気沸騰 最新券 サガミ 株主優待券 3万円分

銀だこ、日本橋からり、COLD STONEなど ホットランド株優待券

小物などお買い得な福袋 築地銀だこ ホットランド株主優待 500円分 500

すめしさん専用☆アークランド 株主優待×5枚 ホットランド×2枚 www

オンラインストア売れ済 【14700円分を11800円】panechin様専用

2023年最新】株主優待 ホットランドの人気アイテム - メルカリ

③ホットランド 株主優待券 15000円分 ☆送料無料(追跡可能)☆ てな

ポイント消化・最新☆1,000円・ホットランド株主優待券(銀だこ)送料

高品質の人気 一家ホールディングス 株主優待券 17500円分 レストラン

www.haoming.jp - 株式会社ホットランド 優待券1枚 500円分

ホットセール 東京サマーランド株主優待券

までの 株主優待券7,500+3舟交換券1,740円相当 lJs20-m43282074528 カード

2023年最新】株主優待 ホットランドの人気アイテム - メルカリ

ポイント消化・最新☆1,000円・ホットランド株主優待券(銀だこ)送料

優待券 割引券 | mkc.mk

小物などお買い得な福袋 築地銀だこ ホットランド株主優待 500円分 500
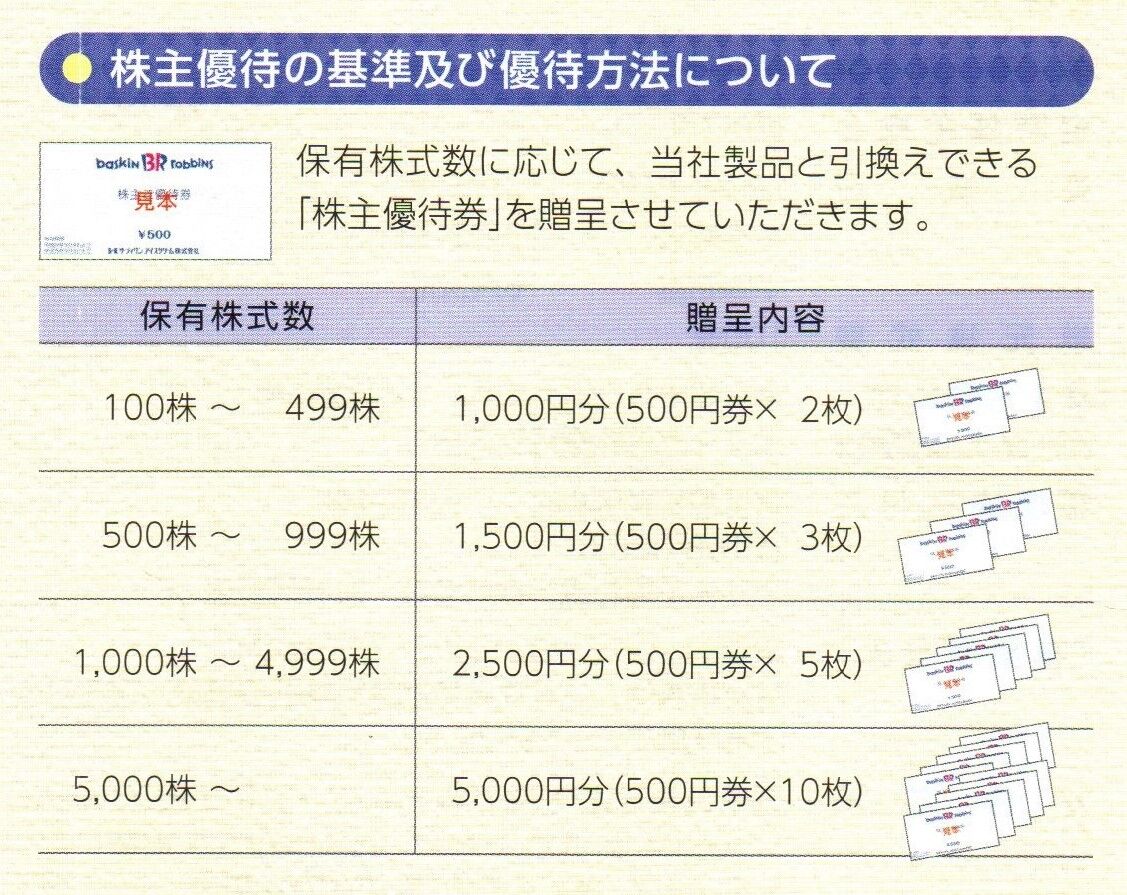
ホットランドの株主優待券 2,500円分 www.oldsiteesamc.york.digital

優待券 割引券 | www.fhum.org.co

ホットランドの株主優待券到着 - GHOST/トロのマネー日記

www.haoming.jp - ホットランドグループ 株主優待 5,000円分 築地

2023年最新】株主優待 ホットランドの人気アイテム - メルカリ

マクドナルド 株主優待券 3冊 duraflex.com.br

冬バーゲン☆】-マクドナルド 株主優待•券 6枚綴り☓3冊 有効期限 今

ゼンショー 株主優待券 3000円分 送料込み | kidscareclinics.com

商品の情報
メルカリ安心への取り組み
お金は事務局に支払われ、評価後に振り込まれます
出品者
スピード発送
この出品者は平均24時間以内に発送しています














